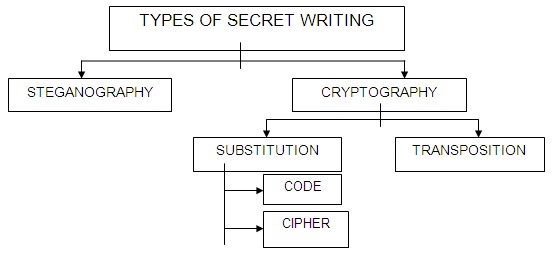
Cryptology consists of code-making and code-breaking. Code-breaking (also known as Cryptanalysis) is the study of analyzing information systems in order to study the hidden aspects of the systems. Code-making (also known as secret writing) can be broken up into two categories: Steganography and Cryptography.
Steganography:
Steganography is secret communication achieved by hiding the existence of a message. This term is derived from the Greek words steganos, meaning "covered," and graphein, meaning "to write." An example would be writing a message in invisible ink. (How to make your own invisible ink.)
Steganography has been proven to be an effective way to communicate secretly. However, steganography suffers from a major weakness. If a messenger carrying a secret message (say written in invisible ink) is captured and someone figures out that the paper carried by the messenger has a message written in invisible ink, then the message can be revealed at once. "Interception of the message immediately compromises all security. Thus, in parallel with the development of steganography, there was the evolution of cryptography" (Singh, 1999, p.6).
The word cryptography is derived from the Greek word kryptos, meaning "hidden." Unlike steganography (where the goal is to hide the existence of a secret message), the goal of cryptography is to hide the meaning of a secret message. In this way, the person sending the message does not entirely care if his or her message is intercepted. Pretend Sally has a message she wants to send to Kurt. Sally writes down her original message (called the original text or plaintext). She then scrambles the message according to a particular protocol which she and Kurt preciously agreed upon. The process by which Sally scrambles the message is called encryption. Encrypted plaintext is known as the ciphertext. Once Sally's message has been encrypted, the message is then sent to Kurt. Since Kurt knows the protocol by which Sally scrambled the message, he can unscramble it (a process known as decryption).
According to Singh (1999, p.7) "Of the two branches of secret communication, cryptography is the more powerful because of this ability to prevent information from falling into enemy hands."
Cryptography itself can be divided into two branches, known as transposition and substitution.In transposition, the letters of the message are simply rearranged, generating an anagram. For example, the letters in the book title Rocket Boys, written by Homer Hickman Jr., can be rearranged to the movie title October Sky (which is a movie made based on the book Rocket Boys)

In substitution, each letter in the plaintext is substituted for a different letter to produce the ciphertext. Hence a substitution cipher is acts in a complementary way to a transposition cipher. Singh (1999, p.9) wrote, "In transposition each letter retains its identity but changes its position. In substitution, each letter changes its identity but retains its position."
There are two main types of substitution: codes and ciphersA code can be defined as substitution at the level of words or phrases. This means that each word is represented by another word or symbol. For example:
LetT = Meeting
D = Tomorrow
19 = Morning
Now, if I write T D 19, the receiver of the code would understand that I mean "meeting tomorrow morning."
(Note: The term encode means to scramble a message using a code. Similarly, the term decode applies to unscrambling an encoded message.)A cipher can be defined as substitution at the level of letters. This means that each letter in my plaintext is substituted for a letter in my ciphertext. For example:
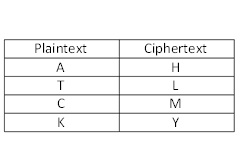
If I write HLLHMY, the receiver of the ciphertext would understand I mean "attack."
(Note: The term encipher means to scramble a message using a cipher. Similarly, the term decipher applies to unscrambling an enciphered message. The terms encrypt and decrypt are more general, and cover scrambling and unscrambling with respect to both codes and ciphers.)